Let’s have a look on the key findings from the research:
- 77% of tested SSL VPNs still use insecure SSLv3, few dozens still have SSLv2
SSLv3 protocol was created in early 1996. Today, it’s considered deprecated, and majority of international and national security standards and compliance norms, such PCI DSS or NIST SP 800-52, prohibit its usage due to numerous vulnerabilities and weaknesses discovered in it during the years. - 76% of tested SSL VPNS use an untrusted SSL certificate
Untrusted certificate allows a remote attacker to impersonate the VPN server, perform Man-in-the-Middle attack, and intercept all the data, including files, emails and password the user pass over the allegedly “secure” VPN connection. The largest risk we observed particularly for SSL VPNs, was due to usage of default pre-installed certificate from the vendor. - 74% of certificates have insecure SHA-1 signature, 5% have even older MD5
Majority of web browsers plan to depreciate and stop accepting SHA-1 signed certificates, as algorithm’s weaknesses can potentially allow forging a certificate, impersonating a server and intercepting critical data. - 41% of SSL VPNs use insecure 1024 key length for their RSA certificates
RSA certificate is used for authentication and encryption key exchange. Since a while already, the RSA key length below 2048 is considered insecure, allowing various attacks. - 10% of SSL VPN servers that rely on OpenSSL (e.g. Fortinet), are still vulnerable to Heartbleed
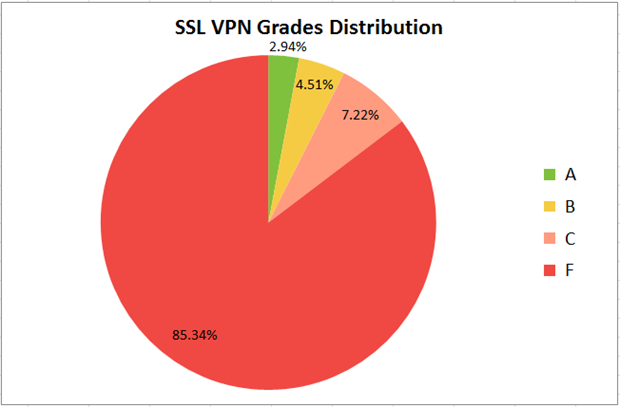
Detected in April 2014, Heartbleed vulnerability affected all products using or relying on OpenSSL, allowing remote non-authenticated attacker to compromise the remote server in few minutes. - Only 3% are compliant with PCI DSS requirements, none is compliant with NIST guidelines
PCI DSS requirements and NIST guidelines can be considered a minimum required level of security.En relation av le comparatif des #VPN de @Korben https://t.co/JRD1IqBNSq Une ressource utile: https://t.co/ShUQah73yu @bizcom @fgrenier
— stéphane koch (@stephanekoch) 24 Février 2016
Article complet : https://www.htbridge.com/blog/90-percent-of-ssl-vpns-use-insecure-or-outdated-encryption.html







